Data decisions are based on policy and pillars
The privacy team works with data stewards, governance, and data authorities to inform and advise in their data use decisions. We create awareness of privacy considerations for units and university stakeholders and connect individuals to appropriate compliance and legal advisers to aide their ability to meet good privacy practices and regulatory compliance.
University privacy policies
- Information Security Policy: Universitywide policy on the use of data, applications, networks and computer systems.
- Campus/University Policies: More information about University of Illinois policies.
- System PCI DSS Policies: Lists of policies that apply to all system and University of Illinois’ merchants in addition to what is included in the PCI DSS
- Social Security Number Policy: Information on the University’s commitment to protecting the privacy of members of the university community.
Terms to know
Commonly used privacy acronyms and their meanings:
| PI – Personal Information | TIA– Transfer Impact Assessment |
| PII – Personally Identifiable Information | DSAR – Data Subject Access Request |
| NPI – Nonpublic Personal Information | PbD – Privacy by Design |
| SPI – Sensitive Personal Information | PIA– Privacy Impact Assessment |
| DPIA – Data Protection Impact Assessment | PIQ – Privacy Impact Questionnaire |
Privacy principles
We are guided by three privacy pillars:
- Trust – Individuals should be able to trust that the university handles their data with the utmost care and protection.
- Transparency – Individuals should be notified and understand how the university collects personal data, and for what processing purpose(s) the data is collected.
- Consent – Individuals should be able to freely consent or withdraw consent wherever practical, and especially when consent is used as the legal basis for collecting and processing personal data.
What’s behind the privacy principles?
The privacy pillars are based upon the Organization for Economic Cooperation and Development’s eight Fair Information Practices Principles. These principles are, summarized:
- Collection limitation: There should be limits to the collection of personal data and it should be lawfully obtained.
- Data quality: Personal data collection should be relevant to the purposes for which it is collected and should be accurate, complete, and kept up to date.
- Purpose specification: The purposes for collecting personal data should be specified at the time of data collection.
- Use limitation: Personal data should not be disclosed, made available or otherwise used for purposes other than those specified, except with the consent of the data subject; or by the authority of law.
- Security safeguards: Personal data should be protected by reasonable security safeguards against such risks as loss or unauthorized access, destruction, use, modification or disclosure of data.
- Openness: There should be a general policy of openness establishing the existence and nature of personal data, and the main purposes of their use.
- Individual participation: Individuals should have the right to obtain data relating to them within a reasonable time, and to request that data be erased, rectified, completed or amended as appropriate.
- Accountability: A data controller should be held accountable to the principles stated above.
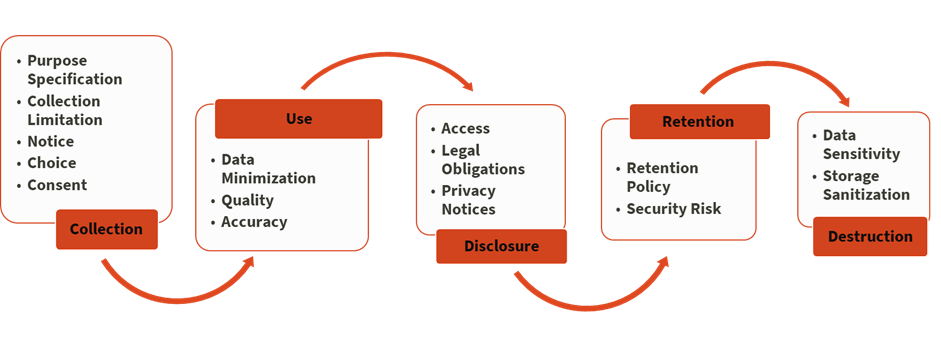
Privacy by design
Collecting personal data brings added responsibilities which can increase requirements, overhead and maintenance costs for new initiatives. Privacy by design is a framework that can be used to reduce project costs and risks while improving default privacy offerings. PbD involves thinking about data throughout its entire lifespan – from collection through destruction. Our team can help you develop plans that consider:
- Data minimization and purpose limitation: Is collecting personal data a requirement for a new offering, or can you reach the same or similar outcomes without collecting data or by using anonymized data? If anonymized data will not meet business requirements, is it possible to limit the amount of data collected? Can the principles of least access and separation of duties minimize access to data? Consider evaluating policies around user access review.
- Full lifecycle protection: How will data that is collected be protected throughout its full lifecycle? Obviously personal data must be encrypted at rest and in flight, but don’t forget to encrypt snapshots, backups and limit writing PII to log files. Consider whether there might be secondary, downstream uses of user data. Keep in mind how long user data can or should be retained per contractual, legal and business requirements?
- Positive-sum, not zero-sum: Could a high standard for privacy result in a competitive advantage and distinguish your offering from similar competing efforts? Would enhancing your default privacy settings also improve your information security posture? Could offering high standards for privacy unlock partnerships with our peers, especially internationally where some countries have stricter privacy regulations?
Privacy regulations
- FERPA: Student records are protected under the Family Education Rights and Privacy Act. The Office of the Registrar manages student record privacy. FERPA-Office of the Registrar
- FOIA: External Relations and Communications at the System Offices processes all Freedom of Information requests to the University of Illinois System or any of the three universities. The Illinois Freedom of Information Act provides public access to government documents and records. FOIA-University of Illinois
- GDPR: Data privacy laws issued by the European Commission, also known as the General Data Protection Regulation, govern data collected from individuals located in the European Union. GDPR – University of Illinois
- HIPAA: The Health Information Portability and Accountability Act protects health information. The University President is responsible for the University’s HIPAA compliance program. The Universitywide Privacy and Security Compliance Council, also known as the HIPAA Subcommittee of the University Information Privacy and Security Committee, is a key part of the President’s oversight effort. HIPAA-University of Illinois System
- IPA: The Identity Protection Act (5 ILCS 179) is an Illinois state law that governs the collection and use of social security numbers by state and local government agencies. It prohibits certain uses of SSNs, creates collection and protection requirements, and requires state agencies, such as the University of Illinois, to enact policy for public view and for employees working with SSNs. IPA – University of Illinois System
- PIPA: Whenever a breach of the security of the data collector’s system data occurs, the Personal Information Protection Act specifically requires public universities, such as the University of Illinois, and other data collectors to notify affected individuals PIPA-UIUC
- PIPL: The University of Illinois Supplemental Privacy Notice – Personal Information Protection Law (“Supplemental Notice – PIPL”) supplements the University of Illinois System Privacy Statement for certain individuals in the People’s Republic of China. PIPL-University of Illinois