| Want to know if the University of Illinois really sent you that email? Call the Technology Services Help Desk at 217-244-7000 and ask! |
Phishing
Phishing is a type of fraudulent communication. A phishing message tries to get the recipient to click a malicious link, call a scammer’s phone number, enter password credentials or send money. Phishing attempts are constantly evolving. Phishing messages can reach us through email, text, voice call, direct message and social media.
Ransomware
Ransomware is a type of malicious software designed to block access to a computer system until a sum of money is paid. These incidents, often involving sensitive or personal information, can result in financial loss and an erosion of trust. There has been an increase in incidents of malicious cyber actors using ransomware to access data.
Don’t get hooked
Like a fisherman using a lure to hook a fish, identity thieves try to lure you into giving up personal information by making what looks like a legitimate request from an organization you trust. These might look like they are from a bank, credit card company or even the university. Unfortunately, phishing scams can be highly effective.
COMMON PHISHING TYPES
Phishing
- Hackers impersonate a real organization or person to obtain your login credentials. You may receive a message asking you to verify your account details with a link that takes you to an imposter login screen that delivers your information directly to the attackers.
Spear Phishing
- Spear phishing is a more sophisticated phishing attack that includes customized information that makes the attacker seem like a legitimate source. They may use your name and phone number and refer to the university in the email to trick you into thinking they have a connection to you, making you more likely to click a link or attachment that they provide.
Whaling
- Whaling is a popular ploy aimed at getting you to transfer money or send sensitive information to an attacker via email by impersonating a real University employee. Using a fake domain that appears similar to ours, they look like normal emails from a high-level official, typically the President, Chancellor, Provost, Dean or CFO, and ask you for sensitive information (including usernames and passwords).
Shared Document Phishing
- You may receive an email that appears to come from a file-sharing sites such as Box, Dropbox or Google Drive alerting you that a document has been shared with you. The link provided in these emails will take you to a fake login page that mimics the real login page and will steal your account credentials.
Vishing
- Vishing (voice phishing) is a form of criminal fraud conducted over the phone. The personal connection can make vishing attacks seem more believable. Cybercriminals typically try to get you to provide private personal and financial information. They also use vishing calls to gather information about an organization and its employees to reap financial rewards.
TO AVOID BEING PHISHED, FOLLOW THESE GUIDELINES
- Keep your password private.
- Only click on or download email attachments from people or companies you know.
- Don’t click on unfamiliar links. Visit official company websites by typing their URL (website address) directly into a browser.
- Read carefully. If a message contains an emotional appeal, like a threat intended to scare you or a plea for help, it may be a scam.
- Don’t reply directly to a suspicious message or use the contact information it provides. If needed, follow up using a different, trusted means of communication, like calling a verified number, starting a new message thread to a known address or visiting a valid website.
- Strangers don’t send millions of dollars to random people (you) on the internet.
DISSECTING A PHISHING MESSAGE
Phishing can be hard to spot
Phishing messages often ask you to click on a link and enter your password or want you to download an attached picture or document. The message may have a sense of urgency, an attempt to pique your curiosity or other appeal to your emotions.
It’s probably a phishing scam if:
- The message is unexpected yet reads like you’ve been having an ongoing conversation.
- You remember when you purchased something or talked to someone. The scammer hopes you don’t remember.
- The message asks you to “update your account” by clicking on a form and entering your password, credit card number, or account number.
- Banks, stores, credit cards and the University of Illinois will never ask you for sensitive information (passwords, account numbers, credit card numbers, etc.) over email.
- The sender’s address is the name of a legitimate company + common email provider. Example: buseybank@hotmail.com
- Banks have their own domains. They don’t send emails from common email providers like @hotmail.com or @gmail.com.
- A few words are turned into a link instead of a long web address.
- Visit a company’s website directly by typing the website address into a browser instead of clicking a button or link.
HOW TO RESPOND
Delete phishing messages immediately. We encourage you to report phishing phone calls and emails: report-spam@illinois.edu.
What does phishing look like?
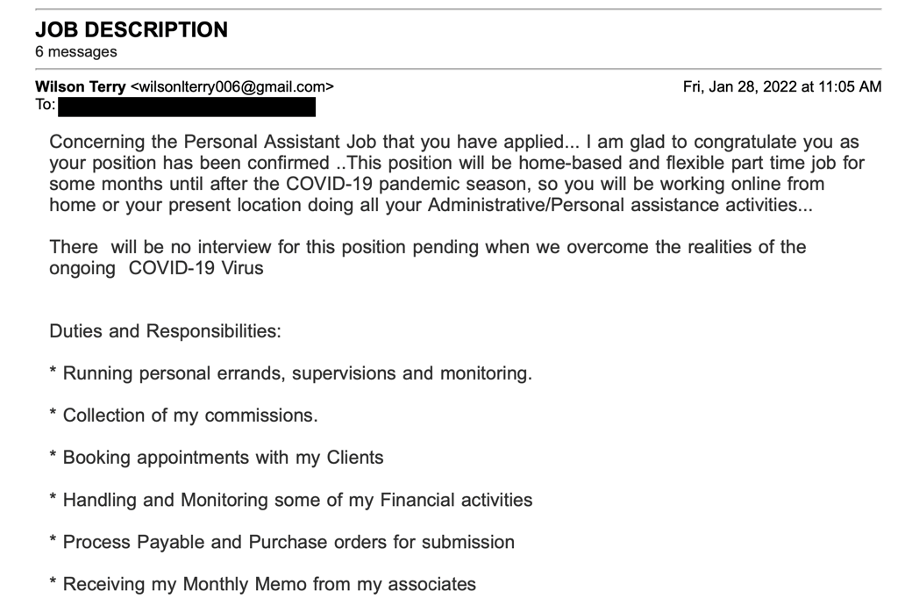

Many phishing attempts targeting universities and students have centered around job scams.
Proofpoint, the university’s contracted vendor for online cybersecurity training, tracks these outbreaks and provided the following information.
- An employment fraud threat involves an attempt to recruit someone under the premise of a legitimate job offer. Threat actors will craft fraudulent job offers, hoping to steal money or personal information, or to recruit an individual to unknowingly comply with illegal activities such as money laundering. Threat actors will typically pose as recruiters or employers and try to entice victims with a variety of opportunities.
- A variation of this scam involves a fake executive personal assistant position with the United Nations Children’s Fund (UNICEF). Spoofed or compromised university email addresses were used to send fake recruitment emails with links to a Google form. Posing as an applicant, a Proofpoint researcher completed the form. The attacker responded, claiming that the “applicant” had been chosen despite no interview taking place.
Ransomware
Ransomware is a type of malicious software designed to block access to a computer system until a sum of money is paid. These incidents, often involving sensitive or personal information, can result in financial loss and an erosion of trust.
There has been an increase in incidents of malicious cyber actors using ransomware to access data.
SPECIAL TIP: Check your software applications for the most recent versions. Outdated apps and operating systems are the target of most ransomware attacks. If your apps need to be updated, you’ll probably be prompted to update them. Go ahead. If there’s an option to automatically update in the future, select that option. Because some apps don’t have auto-updating features, it’s best to check them all.
Ransomware is a serious and increasing threat to all government and private sector organizations, including critical infrastructure organizations. In response, the U.S. government launched StopRansomware.gov, a centralized, whole-of-government webpage providing ransomware resources, guidance and alerts.
AVOID BECOMING A VICTIM
Be careful as you use the internet.
- Verify that attachments and cloud files are safe before opening or downloading, because these files can contain malware (malicious software such as a computer virus) or ransomware.
- To make sure a cloud file or attachment is legitimate, contact the sender through a separate means of communication, such as a known, verified phone number.
- Think before you click. Malware is often sent via phishing message, so be cautious with links in an email, text or direct message. Scammers can fake familiar logos, senders’ names and other information to try to entice you into clicking a malicious link.
- Instead, visit official websites by typing the site address into your browser or using a trusted bookmark.
- Avoid interacting with unexpected pop-up windows. Malicious pop-up windows are a common way to infect devices with malware.
- Try to close unexpected pop-up windows without clicking on the content inside. Consider using a pop-up blocker for additional protection. Check out the Web Browsers – Pop-up Blockers support article for more information.
- If you think your university device has been infected with malware or ransomware, contact security@illinois.edu or call 217-265-0000 as soon as possible. Visit Report a Cybersecurity Incident for additional information.
The Cybersecurity & Infrastructure Agency recommends:
- Know what personal and sensitive information is stored on your systems and who has access to it.
- Limit the data by only storing information you need for business operations.
- Ensure data is properly disposed of when no longer needed.
ADDITIONAL RESOURCES PROVIDED BY THE CYBERSECURITY & INFRASTRUCTURE AGENCY
- For more information and resources on protecting against and responding to ransomware, refer to StopRansomware.gov.